During the process of assigning the network addresses for each of the device in a network system, the use of IP addresses becomes too massive and leads to the wastage of network addresses. In today's topic, we will learn about a network concept that plays an important role in overcoming such a situation. Hi guys and welcome to yet another interesting post by Blueguard. Now without further delay, let's take a look at the agenda for today's topic.
- In the beginning, we will learn about what is subnetting
- Then class addresses and subnet mask
- Then characteristics of subnetting
- Then benefits of subnetting
- Then lastly, drawbacks of subnetting
What is Subnetting
The process of subnetting is to divide the network into smaller network parts. This allows the system to have better connectivity in the system. It also increases the security measures for the network against hacking attempts and also maintains an efficient flow of network traffic.
The smaller divided units of the network are known as subnetworks. Taking an example of an IP address with slash 24 representing the subnet mask can be divided into two subnetworks of slash 25 subnet mask, which can further be divided into smaller subnetworks.
Class Addresses and Subnet Mask
Now that we understand what is subnetting, let's move on to class addresses and subnet mask. Firstly, let's begin with class addresses.
To better understand the subnetting process, we need some information regarding different classes used in IP address, where the first class is class A with a range of 0 to 127, network bits as slash 8. Then we have class P with a range of 128 to 191 with network bits as 16 and lastly we have class C with network range of 192 to 223 with network bits as 24.
The network bits representing each class are very important when making subnets of a particular IP address. Let's see how they do so. For this, we'll be representing each class in binary format. For class A, we have 1 for 8 bits, for class B, 16 bits, and class C, 24 bits.
Moving on, we'll see what exactly is the subnet mask. To better define the subnetworks in the system, we require the use of a subnet mask. That is, the subnet mask is a way to differentiate between the portion of an IP address that represents the network address ID and the host network ID.
In this, let's see the default subnet ask for each of the class. For class A, we have The network ID part is the one that represents the binary digit 1 whereas host ID represents binary digit 0. That means for class A we have 8 bits as network ID and the remaining bits as host ID. By looking at the host ID, we can see that the network addresses that are available for the host is the largest in the class A.
Whereas for class B, we have 16 bits for network ID and the remaining for host ID, where we can see the remaining part for the host ID is lesser than class A. That means class B can assign network IDs for a medium level company.
And lastly for class C, we have 24 bits as network ID and the a look at the characteristics of the subnetting process. First is the network ID, which represents the first IP address in each subnet block. Then we have broadcast ID, which indicates the last IP address of the subnetwork block.
Moving on we have first host ID which is the immediate first IP address after the network ID. Then we have last host ID. As the name suggests it defines the IP address before the broadcast ID.
Continuing, we have next network ID. This defines the network ID of the next subnet block. Then we have the total number of IP addresses in the subnetwork block. And lastly, we have subnet mask or CIDR, which represents the network ID and the host ID part in an IP address.
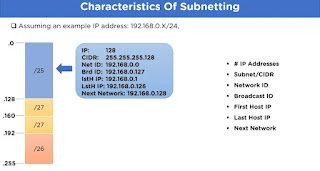
To better understand all the attributes of the subnetting, let's take a look at an example. In this example, we are assuming an IP address 192.168.0.x with the subnet mask of 24. For this IP address, we have divided it into four parts that represent slash 25, slash 27, slash 27 and last part as slash 26. Now let's find out the details that means the attributes for the subnetwork slash 25. The first attribute is the number of IP addresses. Going by the table, we have 0 to 256 addresses in a single block. But in this, slash 25 represents only 0 to 128. That means the total number of addresses in the slash 25 subnet block is 128.
Moving on, we will find out subnet mask or CIDR. That is the default subnet mask of class C which I have taken reference from the subnet table which was explained earlier which is 255.255.255.128.
Then we have the network ID which represents the topmost network address in the subnetwork block. In our case it is 192.168.0.0. Then we have broadcast ID which is the case, it is 192.168.0.127.
Moving on, the network ID and the broadcast ID addresses cannot be assigned to any network device in the network, because the network ID is used to identify the subnetwork block in a network, along with the broadcast ID which is used to communicate with any of the hosts that is connected to the subnetwork block. That also means that the total number of usable network ID addresses in a network block is total number of IP addresses minus 2 that represents network ID and broadcast ID. That would be 128 minus 2 and we get the value 126 which represents the total number of IP addresses that are usable.
Moving on, the next attribute is first host ID. This means the first ID after the network ID which is 192.168.0.1.
Then we have the last host ID which is 192.168.0.126 which is just before the broadcast ID.
And lastly the next network ID, which is 192.168.0.128.
Now that we are clear about all the characteristics of our subnetwork, how about a practice round for everyone to find all the characteristics for the subnetwork block slash 27 subnet mask? You can give your answers in the comment section.
Benefits of Subnetting
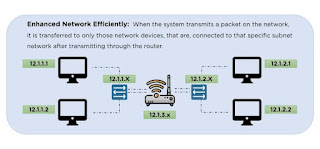
Let's move on to the benefits of using subnetting. The first benefit is enhanced network efficiency; Through the use of applications of subnetting, we can share data to not only a specific portion of the network model rather than broadcasting to the whole network causing unnecessary traffic in the channel as shown in the example.
Over the above picture we see four different hosts and if we want to share a specific data to only two of the hosts we can subnet them into specific parts. Through this, the router will only send data to the specific portion of a sub-network rather than broadcasting to the whole network channel. This will prevent network traffic.
Moving on, the other benefit of using subnetting process is network security. Subnetting also provides protection to an extent against any hacking attempts made on the network model due to the complexity of the subnetworks as presented in the example.
During the hacking attempt, if we can identify how the virus attacks the network model, we can prevent it from attacking all the subnetworks by compromising a single or two of them and preventing the remaining subnetworks.
Drawbacks of Subnetting
Let's move on to the drawbacks of using subnetting process. The very first drawback of using the subnetting process is it makes the network model much more complex, which in turn affects the maintenance and efficiency.
Then we have the unused IP addresses which are left over from applying the network model in a sub-network process.
And lastly we have the low efficiency use of hardware devices. If the hardware devices such as router or switches used are of low efficiency, the performance of the sub-network is also decreased. With this, we have reached the end of this post. If you have any questions regarding the topic, you can ask them in the comments below.
Print this post




.png)

0 Comments